 ,1,2,3, Jia-Ji Li(李家骥)1,2, Wan-Su Bao(鲍皖苏)
,1,2,3, Jia-Ji Li(李家骥)1,2, Wan-Su Bao(鲍皖苏) ,1,2,31Henan Key Laboratory of Quantum Information and Cryptography, SSF IEU, Zhengzhou, Henan 450001,
,1,2,31Henan Key Laboratory of Quantum Information and Cryptography, SSF IEU, Zhengzhou, Henan 450001, 2Synergetic Innovation Center of Quantum Information and Quantum Physics,
First author contact:
Received:2020-01-3Revised:2020-03-12Accepted:2020-03-18Online:2020-05-18

Abstract
Keywords:
PDF (513KB)MetadataMetricsRelated articlesExportEndNote|Ris|BibtexFavorite
Cite this article
Shao-Fu He(何少甫), Yang Wang(汪洋), Jia-Ji Li(李家骥), Wan-Su Bao(鲍皖苏). Asymmetric twin-field quantum key distribution with both statistical and intensity fluctuations. Communications in Theoretical Physics, 2020, 72(6): 065103- doi:10.1088/1572-9494/ab8a11
1. Introduction
The past few decades have witnessed the rapid development of quantum key distribution (QKD) [1]. In this fast-evolving information era, the security of communication is crucial in many scenarios. QKD, whose security is guaranteed by quantum mechanics, provides a reliable platform for two remote users to share secret keys [2, 3]. However, there still remains some practical issues to be handled before the vast application of commercial QKD systems. Among these issues, the point-to-point rate-distance limit of QKD [4, 5] severely restricts the communication distance between legitimate parties. The quantum repeater scheme [6–8] was conjectured to be a perfect solution to this frustrating problem. Unfortunately, current technologies cannot meet the requirement of implementing quantum repeaters experimentally.To overcome the fundamental rate-distance limit of QKD with current quantum communication systems, Lucamarini et al proposed the prospective TF-QKD protocol [9]. The unprecedented TF-QKD protocol enables remote legitimate users to perform secure communications without the restriction of the repeaterless bound. As a similar type of the measurement-device-independent (MDI)-QKD [10, 11], TF-QKD possesses the biggest advantage of MDI-QKD which is the security against attacks on the measurement devices. The secret key rate of TF-QKD scales with the square-root of the channel transmittance η due to the single-photon interference at the untrusted central node. Since the establishment of the original TF-QKD protocol, several variations of TF-QKD type protocols [12–18] and some of their improved versions [19, 20] have been proposed to offer more rigorous security proofs with higher performances. Subsequently, experimental investigations [21–24] are carried out to estimate the practicality of TF-QKD and the results are satisfactory. However, there still exists an inevitable gap between TF-QKD protocols and commercial QKD implementations at present. Recently, several works [25–30] have been done to study the finite-key effect of variant TF-QKD protocols. Moreover, the security of TF-QKD with intensity fluctuations is also examined in [31]. Apart from finite-key effect and intensity fluctuations, protocols with asymmetric losses [32–35] are proposed to test the ability of asymmetrical TF-QKD extensively.
Here, we focus on the asymmetric TF-QKD protocol proposed by Grasselli et al [33]. Developed from the TF-QKD protocol proposed by Curty et al [17], this asymmetric TF-QKD maintains the strengths of the original protocol such as high secret key rate and robustness against phase misalignments. Moreover, this asymmetric TF-QKD protocol is proved to be effective with both decoy-state methods [36–38] and asymmetrical losses. Nonetheless, the secret key rate of the asymmetric TF-QKD protocol is estimated with infinite signal pulses which is infeasible in practical systems [39, 40]. Furthermore, in real-life quantum communication setups, the intensities of the signal pulses are not always steady which would possibly undermine the security of TF-QKD [41–44].
In this paper, we investigate the performance of the asymmetric TF-QKD protocol with finite-key effect and unstable sources cohesively. Here, we provide the modified asymmetric TF-QKD protocol in finite-key regime with intensity fluctuations taken into account. The statistical fluctuations of the parameters are estimated by Azuma’s inequality [45, 46]. With the linear channel loss model, we numerically simulated the secret key rate of the modified asymmetric TF-QKD protocol in the existence of both statistical and intensity fluctuations. Our numerical results demonstrate that both statistical and intensity fluctuations have ineligible influences on the asymmetrical TF-QKD.
This paper is organized as follows. After the above introduction, we provide the actual form of the asymmetric TF-QKD protocol in section
2. Protocol description
Here we focus on an asymmetric TF-QKD protocol [33], in which a three-decoy-state method is utilized to estimate the phase error rate of the raw keys. Considering limited signal pulses, we provide the details of this protocol in finite-key regime while the light sources located in both sides are unstable. The legitimate users Alice and Bob are able to extract an identical secret key string after performing the following steps.2.1. Preparation
At the beginning of this step, Alice and Bob are supposed to choose Z-basis or X-basis for their signal pulses. If Alice (Bob) choose Z-basis with probability ${P}_{{\rm{A}}}^{Z}$ (${P}_{{\rm{B}}}^{Z}$), she (he) prepares a coherent state pulse $\left|\sqrt{{\alpha }_{Z}}{{\rm{e}}}^{{\rm{i}}\pi {b}_{{\rm{A}}}}\right\rangle $ ($\left|\sqrt{{\beta }_{Z}}{{\rm{e}}}^{{\rm{i}}\pi {b}_{{\rm{B}}}}\right\rangle $) as a signal state, where ${\alpha }_{Z}$ (${\beta }_{Z}$) is the intensity of Alice’s (Bob’s) signal state pulse, bA (bB) denotes the random bit selected from the set $\left\{0,1\right\}$. If X-basis is chosen with probability $1-{P}_{{\rm{A}}}^{Z}$ ($1-{P}_{{\rm{B}}}^{Z}$), Alice (Bob) emits a phase randomized coherent state as a decoy state whose average intensity is chosen from the set ${\alpha }_{a}\in \left\{{\alpha }_{0},{\alpha }_{1},{\alpha }_{2}\right\}$ (${\beta }_{b}\in \left\{{\beta }_{0},{\beta }_{1},{\beta }_{2}\right\}$) with probabilities Pa (Pb), where $a,b\in \left\{0,1,2\right\}$ . However, the photon sources are unstable. As a result, the intensities of both signal and decoy states are fluctuating around their average values.2.2. Measurement
After the preparation step, the signal pulses are sent to an untrusted central node Charlie through quantum channels. The channel transmittances from Alice to Charlie and Bob to Charlie are denoted as ${\eta }_{{\rm{A}}}$ and ${\eta }_{{\rm{B}}}$. Charlie is supposed to perform the measurements using a beamsplitter with two threshold detectors L and R. At this moment, the untrusted third party Charlie has no information whether the signal pulse is a signal state or a decoy state. Then, Charlie announces the output of the two detectors.2.3. Sifting
The first two steps are supposed to be repeated for N rounds by the two legitimate parties. Here, the measurement results corresponding to only one of the two detectors clicks are called successful detection events. After that, Alice and Bob announce their choices of the basis and intensities to each other through an authenticated public channel. The successful detection events corresponding to the same basic choices are maintained for the following steps.2.4. Parameter estimation
The total amount of Z-basis and X-basis successful detection events are denoted as sZ and sX. According to the decoy state intensities αa and βb they have chosen, Alice and Bob are able to obtain the detailed amount of sab of the X-basis successful detection events. Particularly, the random bits bA and bB of the Z-basis successful detection events are utilized to extract the final key. In our protocol, Bob always flips his bit bB for an R detector click. Importantly, the total amount of successful detection events are exploited to estimate the phase error rate eph.2.5. Postprocessing
In this step, Alice firstly sends Bob leakEC bits to perform error correction using an information reconciliation scheme. Next, Alice exploits $\mathrm{log}\left(1/{\varepsilon }_{\mathrm{cor}}\right)$ bits to compute a hash of her raw key string. Then the hash and the random two-universal hash function are sent to Bob through the authenticated public channel. Bob computes the hash of his string to ensure that their key bits are identical. Finally, Alice and Bob utilize a random two-universal hash function to perform privacy amplification. After that, they are able to obtain two key strings KA and KB with secret key length L.3. Methods
Before we demonstrate the parameter estimation methods, it is necessary to characterize the security of the protocol at first. Here, the universally composable framework is utilized in this section [30, 47, 48]. The security of a QKD protocol can be ensured by two criterions ‘correctness’ and ‘secrecy’. For two small errors ${\varepsilon }_{\mathrm{cor}}$ and ϵsec, the protocol is ϵcor-correct and ϵsec-secret if the following two conditions are satisfied: (1) $\Pr \left[{K}_{{\rm{A}}}\ne {K}_{{\rm{B}}}\right]\leqslant {\varepsilon }_{\mathrm{cor}}$. (2) $\tfrac{1}{2}{\parallel {\rho }_{{K}_{{\rm{A}}}{\rm{E}}}-{U}_{{K}_{{\rm{A}}}}\otimes {\rho }_{{\rm{E}}}\parallel }_{1}\leqslant {\varepsilon }_{\sec }$. Notably, ${\parallel \cdot \parallel }_{1}$ is the trace norm and ${\rho }_{{K}_{{\rm{A}}}{\rm{E}}}$ is the joint state of Alice and Eve. ${U}_{{K}_{{\rm{A}}}}$ is the mixed state of all possible values of ${K}_{{\rm{A}}}$ while ${U}_{{K}_{{\rm{A}}}}\otimes {\rho }_{{\rm{E}}}$ describes the ideal case. A QKD protocol can be described as ϵ-secure if it is both ϵcor-correct and ϵsec-secret with $\varepsilon ={\varepsilon }_{\mathrm{cor}}+{\varepsilon }_{\sec }$.In our parameter estimation, the effect of statistical fluctuations and intensity fluctuations are taken into account concurrently. As mentioned in the above section, the total amounts of successful detection events sZ, sX as well as sab are directly observed by Alice and Bob. With these successful detection events acquired in the real protocol, the two users are able to estimate the secret key rate employing our methods.
At the beginning of our methods, we need to estimate the effect of statistical fluctuations. Although we can directly obtain the observed values of ${s}_{{ab}}$ in real experiments, the expectation values of these successful detection events are remained unknown. In the case with stable sources, the malicious eavesdropper Eve cannot acquire the intensity choices of the signal pulses due to the decoy-state method. Therefore, we can assume that the trials are independent with each other and every detection event can be regarded as an independent random variable. In this case, finite-key analysis tools such as Chernoff bound [49] and Hoeffding’s inequality [50] can be utilized to estimate the statistical fluctuations of successful detection events. Unfortunately, considering the existence of unstable sources, the eavesdropper Eve can carry out a coherent attack strategy. Eve first make all the pulses interact coherently with an auxiliary system, then she utilizes the information Alice and Bob announced in the sifting step to measure the auxiliary. Thus, the prerequisite that the detection events are independent random variables is not satisfied and both Chernoff bound [49] and Hoeffding’s inequality [50] are invalid then. In order to estimate the finite-key effect of the asymmetric TF-QKD with unstable sources, we utilize Azuma’s inequality [45, 46] which is suitable for a sequence of dependent random variables which can be correlated in anyway if the sequence is a martingale and satisfies the bounded difference condition.
Let n0, n1, ⋯, nN be a sequence of random variables, the two conditions martingale and bounded difference condition can be expressed as follows:
(i) Martingale. If and only if the expectation value of ${n}_{i+1}$ conditioned on the first i+1 outcomes of n0, n1, ⋯, ni satisfies $E\left[{n}_{i+1}| {n}_{0},{n}_{1},\cdots ,\,{n}_{i}\right]={n}_{i}$ for all non-negative integer i, the sequence can be regarded as a martingale.
(ii) Bounded difference condition. The bounded difference condition is satisfied if there exists ${c}_{i}\gt 0$ such that $\left|{n}_{i+1}-{n}_{i}\right|\leqslant {c}_{i}$ for all non-negative integer i.
For the sequence n0, n1, ⋯, nN which contains N+1 trials and satisfies the above conditions with ci=1, nN can be bounded by Azuma’s inequality [45, 46]
In order to apply Azuma’s inequality to our protocol, we first set m0, m1, ⋯ , mN as N+1 random but dependent variables that satisfies ${m}_{j}\in \left\{0,1\right\}$. Then we denote ${s}_{i}={\sum }_{j=1}^{i}{m}_{j}$ as the observed value and ${s}_{i}^{* }={\sum }_{j=1}^{i}P\left({m}_{j}| {m}_{0},{m}_{1},\cdots ,\,{m}_{j-1}\right)$ as the expectation value of m1, ⋯ , mi respectively. Next, we define the ith trial of the sequence n0, n1, ⋯, nN as
In the modified asymmetric TF-QKD protocol, every detection event can be regarded as a random variable, the total trials can be regarded as a sequence with N random variables. The successful detection event sab can be regarded as an observed output of the sequence. We denote ${s}_{{ab}}^{* }$ as the expectation value of the sequence. Then sN and ${s}_{N}^{* }$ in equation (
In the modified asymmetric TF-QKD protocol, the expectation values ${s}_{{ab}}^{* }$ can be utilized to estimate the yields of the X-basis with
Consequently, one can utilize the observed values sab together with Azuma’s inequality to rewrite equation (
After that, we have obtained the expectation value of the successful detection events ${s}_{{ab}}^{* }$ with statistical fluctuations taken into account. However, intensity fluctuations not only affect the correlation between detection events, but also change the actual value of the intensities. In our protocol with unstable sources, we suppose that the largest intensity fluctuation magnitudes of the photon pulses emitted by Alice and Bob are δA and δB separately. Then we can acquire the upper bound and lower bound of the intensities of their signal states and decoy states by
Now we have obtained the upper bound of the phase error rate with our parameter estimation methods. On the other hand, the bit error rate ebit of the raw key bits can be directly obtained by Alice and Bob in the error correction step. Finally, according to [30], the ultimate secret key length can be given by
4. Simulations
In this section, we numerically simulate the performance of the asymmetric TF-QKD protocol with both statistical and intensity fluctuations. The secret key rate of the protocol can be obtained by R=L/N with the secret key length L estimated above. The linear channel loss model of asymmetric TF-QKD presented in [33] is adopted to simulate the observed values which can be measured in real experiments by the communication parties. In our simulations, the dark count rate and the error correction inefficiency are fixed to ${P}_{d}={10}^{-8}$ and f=1.1 respectively.To compare the performance of the modified asymmetric TF-QKD protocol under different circumstances, we plot the secret key rate as a function of the overall loss between Alice and Bob which is measured in dB. The intensities of the signal-states are optimized over the asymmetrical losses while the intensities of the decoy-states are set to ${\alpha }_{0}={\beta }_{0}=0.5$, ${\alpha }_{1}={\beta }_{1}={10}^{-2}$ and ${\alpha }_{2}={\beta }_{2}={10}^{-4}$ for Alice and Bob. For convenience, the magnitudes that we utilized to characterize the phase and polarization misalignments are set to 2%. In addition, the PLOB bound [5] is exploited as the yardstick when describing the performances of the secret key rates. Moreover, we fix the security bounds to ${\varepsilon }_{\sec }={10}^{-10}$ and ${\varepsilon }_{\mathrm{cor}}={10}^{-15}$.
In figure 1, we demonstrate the effect of intensity fluctuations with both symmetrical and asymmetrical losses. In the case with symmetrical losses, the secret key rate is robust against intensity fluctuations. As shown in figure 1(a), the symmetric TF-QKD protocol can beat the PLOB bound with all three intensity fluctuation magnitudes. However, the secret key rate of the asymmetric TF-QKD protocol is much lower comparing with the former case. Figure 1(b) demonstrates that the protocol can hardly beat the PLOB bound when the intensity fluctuation magnitudes of Alice and Bob are larger than 20%.
Figure 1.
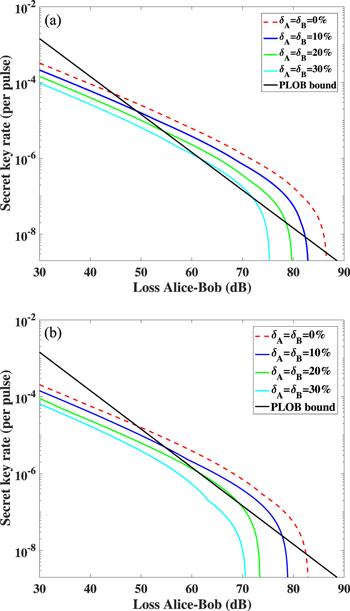 New window|Download| PPT slide
New window|Download| PPT slideFigure 1.Secret key rate as a function of the overall loss between Alice and Bob with symmetrical and asymmetrical losses. (a) The loss between Alice and Charlie is the same as Bob’s side. (b) The loss between Alice and Charlie is always 10 dB larger than the loss between Bob and Charlie. The total amount of signal pulses are set to $N={10}^{14}$. In both (a) and (b), the intensity fluctuation magnitudes of Alice’s and Bob’s photon sources are set to 30%, 20% and 10% (curves from left to right). The dashed line characterizes the case with no intensity fluctuations.
In order to study the finite-key effect with unstable sources, we compare the performances of the protocol with different amount of total signal pulses. Here, four different total amounts of signal pulses are utilized to estimate the secret key rates. As shown in figure 2, statistical fluctuations have an extremely significant impact on the secret key rate when the photon sources are unstable. In this case, the protocol cannot overcome the PLOB bound if the total signal pulses are limited. Thus, we have to ensure that the two parties emit enough signal pulses in long distance communications.
Figure 2.
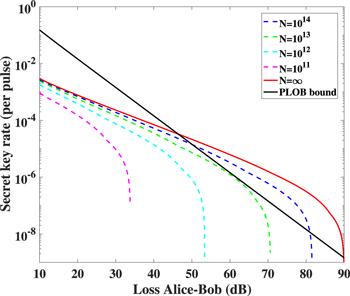 New window|Download| PPT slide
New window|Download| PPT slideFigure 2.Secret key rate in logarithmic scale as a function of the overall loss between Alice and Bob with different amount of total signal pulses. In this plot, the loss between Alice and Charlie is always 5 dB larger than the loss between Bob and Charlie. The intensity fluctuation magnitudes of Alice’s and Bob’s photon sources are set to 10%. The aggregate amount of photon pulses are set to ${10}^{11}$, ${10}^{12}$, ${10}^{13}$ and ${10}^{14}$ (dashed curves from left to right). The solid curve represents the case with infinite signal pulses.
Additionally, we compare the secret key rate when the intensity fluctuation magnitudes of Alice’s and Bob’s photon sources are different. We first set the intensity fluctuation magnitudes to ${\delta }_{{\rm{A}}}=40 \% $ (${\delta }_{{\rm{B}}}=20 \% $) and ${\delta }_{{\rm{A}}}=20 \% $ (${\delta }_{{\rm{B}}}=0 \% $) as the dotted lines from left to right in figure 3. Then we exchange the intensity fluctuation magnitudes of Alice and Bob with ${\delta }_{{\rm{A}}}=20 \% $ (${\delta }_{{\rm{B}}}=40 \% $) and ${\delta }_{{\rm{A}}}=0 \% $ (${\delta }_{{\rm{B}}}=20 \% $). The results are characterized by the dashed lines close to the dotted lines. As shown in figure 3, the effects of intensity fluctuations of Alice’s and Bob’s are not the identical in the asymmetrical case.
Figure 3.
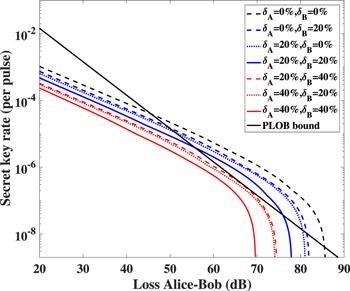 New window|Download| PPT slide
New window|Download| PPT slideFigure 3.Secret key rate in logarithmic scale as a function of the overall loss between Alice and Bob with asymmetrical intensity fluctuation magnitudes. The dashed line on the far right represents the case with no intensity fluctuations. The total amount of signal pulses are set to N=1014 while the loss of Alice–Charlie is always 5 dB larger than Bob–Charlie.
Our simulation results suggest that the asymmetric TF-QKD protocol is still capable to beat the repeaterless bound with statistical and intensity fluctuations. However, the effects can be very significant if the data size is small. Thus, in order to obtain higher secret key rates in long-distance communications, the legitimate users are supposed to send adequate signal pulses and exploit photon sources with lower intensity fluctuation magnitudes.
5. Conclusion
In this paper, we have analyzed the asymmetric TF-QKD protocol with both statistical and intensity fluctuations. We proposed the modified asymmetric TF-QKD protocol with finite signal pulses and unstable sources. In order to estimate the statistical fluctuations, we utilized Azuma’s inequality to obtain the upper and lower bounds of the observed successful detection events. The secret key rate is obtained by numerically optimizing the phase error rate over all possible intensities. Furthermore, we simulated the performance of the protocol with finite-key length and fluctuating intensities. The simulation results indicate that statistical and intensity fluctuations cannot be neglected in asymmetric TF-QKD especially with long communication distances. In summary, our results in this paper could provide a theoretical reference for the future applications of TF-QKD.Acknowledgments
Project supported by National Natural Science Foundation of China (61675235, 61605248 and 61505261) and National Key Research and Development Program of China (2016YFA0302600).Reference By original order
By published year
By cited within times
By Impact factor
[Cited within: 1]
DOI:10.1038/nphoton.2014.149 [Cited within: 1]
DOI:10.1103/RevModPhys.81.1301 [Cited within: 1]
DOI:10.1038/ncomms6235 [Cited within: 1]
DOI:10.1038/ncomms15043 [Cited within: 2]
DOI:10.1103/PhysRevLett.81.5932 [Cited within: 1]
DOI:10.1038/35106500
DOI:10.1103/RevModPhys.83.33 [Cited within: 1]
DOI:10.1038/s41586-018-0066-6 [Cited within: 1]
DOI:10.1103/PhysRevLett.108.130502 [Cited within: 1]
DOI:10.1103/PhysRevLett.108.130503 [Cited within: 1]
DOI:10.1103/PhysRevA.98.062323 [Cited within: 1]
DOI:10.1103/PhysRevX.8.031043
DOI:10.1103/PhysRevApplied.11.034053
DOI:10.1038/s41534-019-0175-6
DOI:10.1103/PhysRevA.98.042332 [Cited within: 1]
DOI:10.1038/s41598-019-39454-1 [Cited within: 1]
DOI:10.1103/PhysRevA.100.022306 [Cited within: 1]
DOI:10.1088/1367-2630/ab2b00 [Cited within: 1]
DOI:10.1038/s41566-019-0377-7 [Cited within: 1]
DOI:10.1103/PhysRevX.9.021046
DOI:10.1103/PhysRevLett.123.100505
DOI:10.1103/PhysRevLett.123.100506 [Cited within: 1]
DOI:10.1038/s41598-019-39225-y [Cited within: 1]
DOI:10.1038/s41598-019-53435-4
DOI:10.1103/PhysRevApplied.12.024061
DOI:10.1038/s41467-019-11008-z
[Cited within: 3]
DOI:10.1088/1367-2630/ab5a97 [Cited within: 1]
DOI:10.1103/PhysRevA.99.062316 [Cited within: 1]
DOI:10.1088/1367-2630/ab520e [Cited within: 5]
DOI:10.1103/PhysRevA.100.062337
DOI:10.1088/1367-2630/ab623a [Cited within: 1]
DOI:10.1103/PhysRevLett.91.057901 [Cited within: 1]
DOI:10.1103/PhysRevLett.94.230503
DOI:10.1103/PhysRevLett.94.230504 [Cited within: 1]
DOI:10.1038/ncomms4732 [Cited within: 1]
DOI:10.1038/ncomms1631 [Cited within: 1]
DOI:10.1103/PhysRevA.75.052301 [Cited within: 1]
DOI:10.1088/1367-2630/11/7/075006
DOI:10.1103/PhysRevA.94.032335
DOI:10.1364/JOSAB.36.000B83 [Cited within: 1]
DOI:10.2748/tmj/1178243286 [Cited within: 4]
DOI:10.1088/1367-2630/17/9/093011 [Cited within: 4]
DOI:10.1103/PhysRevA.89.022307 [Cited within: 1]
DOI:10.1103/PhysRevLett.100.200501 [Cited within: 1]
DOI:10.1214/aoms/1177729330 [Cited within: 2]
DOI:10.1080/01621459.1963.10500830 [Cited within: 2]
