 ,21 Power Generation Company, GuangZhou 510700,
,21 Power Generation Company, GuangZhou 510700, 2 Anhui Qasky Quantum Technology Co., Ltd., Wuhu 241102,
Received:2020-05-20Revised:2020-09-10Accepted:2020-09-10Online:2020-10-27

Abstract
Keywords:
PDF (488KB)MetadataMetricsRelated articlesExportEndNote|Ris|BibtexFavorite
Cite this article
Meng Ye, Jian-Hui Li, Yong Wang, Peng Gao, Xin-Xin Lu, Yong-Jun Qian. Quantum key distribution system against the probabilistic faint after-gate attack. Communications in Theoretical Physics[J], 2020, 72(11): 115102- doi:10.1088/1572-9494/abb7d8
1. Introduction
Quantum key distribution (QKD) enables two legitimate parties, Alice and Bob, to share a series of secure keys [1]. The unconditional security of QKD protocols, such as BB84, has been proven in theory [2 –5]. However, the components used for experimental realization of QKD system deviate from the models in the original security proofs. The imperfect components, such as the source, modulators or detectors, may leave loopholes that the eavesdroppers (Eve) can exploit to steal the secure keys [6 –24]. A single photon-detector (SPD) is a complex equipment at the measurement side, which is vulnerable to a serious of detector-related attacks [10 –23]. A typical example is detector blinding attack [12 –17]. Eve blinds the SPD by injecting bright illumination into the SPDs, and converts them into linear detectors which are not sensitive to single photon. Then Eve can use bright trigger pulses to remotely control the response of the SPDs, thereby stealing almost all key information without evidently increasing errors. Particularly, in a faint after-gate attack [19], Eve does not need to blind the SPD in advance, and the trigger pulses (≤120 photons/pulse) are weaker than the ones in detector blinding attack. Eve makes the trigger pulses arrive at the falling edge of the gate to control the response of the SPDs, thus stealing the key information.To defense the faint after-gate attack, measurement device independent protocol is a promising approach that can close all loopholes from the measurement unit, however, the challenge is that the approach requires a two-photon interference [25]. Another approach is improving the practical QKD systems with security patches [26]. Since the faint after-gate attack leads to abnormally high photocurrent, monitoring the high current is a possible solution to reveal this attack [27 –29]. However, this solution depends on the precision of monitoring instrument, if the photocurrent increased by an attack is below the detectable bound, the countermeasure seems to fail to detect Eve’s presence. Based on the idea, we establish a model, called probabilistic faint after-gate attack model. If Eve partially implement the faint after-gate attack with a certain probability, she can still obtain information without being detected if the photocurrent increased by the attack is less than the detectable range.
Then we propose a countermeasure. As the open question is how to guarantee the practical security of QKD systems when the photocurrent is under the detectable boundary. The countermeasure gives a method of how to define the detectable bound with practical instrument. Furthermore, under the detectable bound we analyze the security of QKD system in view of the weak randomness model [30], and give a method of removing the information that Eve steals. Some quantum hacking can be described by the weak randomness model, which is proposed by Li et al [30 –33]. In the QKD system, Alice and Bob use true random number generators to prepare and measure the quantum states. The input random numbers which is entered into the quantum device control the classical bit encoding and the bases selection. If the random number is perfect, Eve has no prior knowledge about state preparation and measurement bases choice. However, if the random number is controlled or leaked to Eve, Eve can utilize the loophole to implement quantum hacking and steal the key. For example, in a wavelength attack [9], Eve can use different wavelengths to control the measurement bases selection, which can be treated as the process that the random number for selecting the measurement base is partly controlled by Eve. Similarly, in a time-shift attack [11], Eve can utilize different photon arrival times to control the time-dependent efficiency of two SPDs with different bit encoding. A part of random numbers for state preparation are thus known or controlled by Eve.
The paper is organized as follows. Section
2. Probabilistic faint after-gate attack model
In this section, we firstly briefly review the original faint after-gate attack [19] The key device of SPD in most commercial QKD systems is avalanche photodiode (APD) [34]. Most of the SPDs operate in gated-mode. When the gate is on, the APD is reverse-biased above the breakdown voltage Vb, SPD is in Geiger mode and sensitive to the single photon. When the gate is off, the APD is reverse-biased below Vb, SPD is in linear mode and cannot detect the single photon. In normal operation, SPD can detect single photon, the quantum state arrives in the gate and generate a click with a detection probability. However, the gate signal is not perfect, the falling edge of the gate is not instantaneous, but has a certain width. In the region, SPD is not sensitive to the single photon pulse, but can detect bright trigger pulse. The detection probability is superlinear to the intensity of the bright trigger pulse: for a factor of two (3 dB) decrease in the intensity of trigger pulse, the detection probability drops steeply from high to low probability, the ratio of the detection probabilities is much larger than 2. The gaps between ideal models and imperfect devices would leave loopholes for Eve, she can exploit the loophole to implement the faint after-gate attack. Taking a polarization-encoding BB84 as an example, the attack process can be described as follows:(1) Alice randomly modulates quantum states from the chosen of four polarization(2) Based on the detection result, Eve (Faked-Alice) resends bright trigger pulses instead of single photon pulses, and makes them arrive at the falling edge of the gate. As the superlinearity of the SPD, Bob will detect the bright trigger pulses sent by Eve with a high probability if he uses the same basis as Eve, and otherwise, with incompatible bases, half of the power of the bright trigger pulses hits the conjugate basis detectors, and cause low probability to be detected.
(3) After Alice and Bob publicly announce basis choice and retain the identical choices, Eve can obtain the basis alignment information from the public channel and sift the measurement result. Therefore, the basis modulated by Eve will be either equal to or different with the basis modulated by Bob. If the modulated bases are equal, Eve can obtain almost all the information about the keys. If the modulated bases differ, the SPD clicks at Bob may introduce tiny error counts since the detection probability is low, thereby not increasing the quantum bit error rate (QBER) evidently. Some researchers find that the APD photocurrent is anomalously higher than the one in normal operation [27 –29]. Monitoring the photocurrent is the intuitive countermeasure against the faint after-gate.
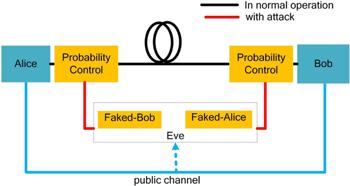
Based on the principle of faint after-gate attack, the target components of probabilistic faint after-gate attack is APD single-photon detectors for gated-mode. Figure 1 shows the schematic of the probabilistic faint after-gate attack. The black lines depict the original quantum channel in normal QKD system. The red lines depict the eavesdropping channel established by Eve. The blue lines depict the composition of the public channel. Eve can obtain the basis alignment information from the public channel. Similarly, Eve (Faked-Bob) probabilistically intercepts the signal from Alice and randomly chooses one of two bases to measure. Compared with the original faint after-gate attack, the Probability Control module is added to control the number of times Eve intercepts the quantum states. Based on the detection result, Eve (Faked-Alice) modulates the corresponding polarization to the bright trigger pulse with specific optical power, and resends to Bob at the falling edge of the gate. The Probability Control module controls the number of times that Eve resends the bright trigger pulses. Therefore, the signals received at Bob’s side have two parts: the bright trigger pulses sent by Eve and the normal single-photon signals transmitted from Alice. After Alice and Bob publicly announce basis choice and retain the identical choices, Eve can eavesdrop part of the key information, which depends on the frequency of attack. If the probability is 100%, the attack is the original faint after-gate attack, and it leads to obviously high photocurrent [27 –29], we can use the countermeasure of monitoring photocurrent to detect Eve. However, if the probability of attack times is small enough, photocurrent monitoring may not reveal the eavesdropper due to limited precision of the monitoring instrument.
Figure 1.
 New window|Download| PPT slide
New window|Download| PPT slideFigure 1.Schematic of the probabilistic faint after-gate attack. Alice and Bob are legitimate communicate parties. For Alice, Eve is the role of Faked-Bob. For Bob, Eve plays the role of Faked-Alice. Probability control is the module that controls the Eve’s frequency of attack.
3. Countermeasure with weak randomness
To explore the security during the probabilistic faint after-gate attack, the countermeasure is as follows. First, the detectable bound of the photocurrent monitoring strategy is defined with a practical monitoring instrument. For the case that the photocurrent is above the detectable bound, this will trigger the alarm. Alice and Bob discard the keys of the time period. For the case that the photocurrent is below the detectable bound, the information that Eve steals can be estimated correctly; thus, Alice and Bob can still obtain the secure key after removing the information by the post-processing method.For the photocurrent monitoring instrument, we define I0 as the photocurrent in a normal QKD system and I1 as the photocurrent during a probabilistic faint after-gate attack with 100% probability. The probability that Eve resends the bright trigger pulses in all received bits at Bob’s SPD is defined as Ba . The precision of the instrument to monitor the photocurrent is larger than p . The photocurrent monitoring instrument can detect the probabilistic blinding attack if their relationship satisfies
The minimum probability to resend the bright trigger pulses by Eve in all received bits at Bob’s SPD is defined as Bamin, which satisfies
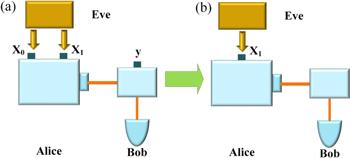
We analyze the security of a probabilistic faint after-gate attack using a weak randomness model. The weak randomness model is shown in figure 2 (a) [30], and there are two random input bits X0 and X1 in Alice’s side, which are used to select state preparation of encoding classical bits and bases, respectively. At Bob’s side, there is one random input bit y for the selection of state measurement basis. Alice and Bob publicly announce basis choice and retain the identical choice, which means the random input bits X1 and y are equivalent after the sifting process. For convenience, we can only assume X0 and X1 to control the selection of encoding classical bit and bases. The weak randomness model can be viewed as the case that Eve plants hidden variable into quantum devices to control X0 and X1 .
Figure 2.
 New window|Download| PPT slide
New window|Download| PPT slideFigure 2.(a) Weak randomness model, there are two random input bits X0 and X1 at Alice’s side. At Bob’s side, there is one random input bit y, where X0 refers the random input bits to the selection of classical encoding bit, X1 refers the random input bits to the selection of preparation bases at Alice’s side, y refers to the random input bits to the selection of measurement bases at Bob’s side. (b) Weak randomness model of probabilistic faint after-gate attack, Eve plants hidden variable λ1 into Alice’s side to control X1, where X1 refers the random input bits to the selection of preparation bases at Alice’s side.
For a probabilistic faint after-gate attack, in the intercept process, Eve randomly chooses bases to measure the quantum states from Alice, and then Eve resends the bright trigger pulses to Bob’s SPD, the pulse will be detected at a high probability if Eve chooses the right basis, otherwise it will be detected at a low probability if Eve chooses the wrong basis. In the weak randomness model, Eve plants hidden variable into Bob’s quantum device to control the measurement basis selection. According to the aforementioned simplification of the model, this is equivalent that Eve plants a hidden variable λ1 into Alice’s quantum device to control the random input bits X1, which is shown in figure 2 (b). This variable satisfies
The weak randomness model can describe the case that the QKD system is under a probabilistic faint after-gate attack using the countermeasure of monitoring photocurrent. For a prepare-and-measure QKD protocol, we apply entanglement distillation and purification technology [35] to analyze the security. Alice prepares maximally entangled state
Since the behavior of Eve in the Pauli channel will increase the bit error rate ebj and phase error rate epj, their expression can be given, respectively, as
For the hidden variable controlled by Eve
Then, the secret key rate with
With
With equation (
Figure 3.
 New window|Download| PPT slide
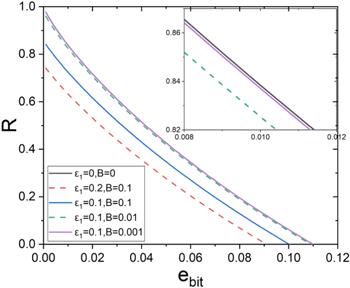
New window|Download| PPT slideFigure 3.Secure key rate for different detectable bound B and randomness deviation parameters ϵ1 . The black solid line(ϵ1 =0, B =0) is described the case without faint after-gate attack.
4. Conclusion
In conclusion, we proposed a probabilistic faint after-gate attack, since the practical monitoring instrument in real-life have limited measurement precision. It is a general attack for APDs single-photon detectors and suitable for the operation mode of gated-mode. Moreover, we give a countermeasure which can define the detectable bound with the practical monitoring instrument. When the probability of a probabilistic faint after-gate attack is above the detectable bound, the monitoring approach is effective to detect Eve. If the probability is below the detectable bound, with the weak randomness model, we can estimate the maximal amount of the information that Eve obtain, then we can employ the post-processing method to remove it. This framework can be applied to analyze the practical security in QKD system with limited instrument precision.Reference By original order
By published year
By cited within times
By Impact factor
[Cited within: 1]
DOI:10.1126/science.283.5410.2050 [Cited within: 1]
DOI:10.1103/RevModPhys.74.145
DOI:10.5555/2011586.2011587
DOI:10.1140/epjd/e2007-00010-4 [Cited within: 1]
DOI:10.1103/RevModPhys.81.1301 [Cited within: 1]
DOI:10.1088/1367-2630/4/1/344
DOI:10.1088/1367-2630/12/11/113026
DOI:10.1103/PhysRevA.84.062308 [Cited within: 1]
[Cited within: 1]
DOI:10.1103/PhysRevA.78.042333 [Cited within: 1]
DOI:10.1038/nphoton.2010.214 [Cited within: 1]
DOI:10.1038/ncomms1348
DOI:10.1364/OE.18.027938
DOI:10.1088/1367-2630/11/6/065003
DOI:10.1364/OE.19.023590
DOI:10.1103/PhysRevA.88.062335 [Cited within: 1]
DOI:10.1088/1367-2630/13/1/013043
DOI:10.1103/PhysRevA.84.032320 [Cited within: 2]
DOI:10.1088/1367-2630/13/11/113042
DOI:10.1088/1367-2630/13/7/073024
DOI:10.1103/PhysRevLett.112.070503
DOI:10.1103/PhysRevApplied.10.064062 [Cited within: 1]
DOI:10.1103/RevModPhys.92.025002 [Cited within: 1]
DOI:10.1103/PhysRevLett.108.130503 [Cited within: 1]
DOI:10.1038/nphoton.2014.149 [Cited within: 1]
DOI:10.1063/1.3597221 [Cited within: 3]
DOI:10.1063/1.3658806
DOI:10.1063/1.3658806 [Cited within: 3]
DOI:10.1038/srep16200 [Cited within: 3]
DOI:10.1007/s11128-018-1830-0
DOI:10.1364/OL.44.001226
DOI:10.1103/PhysRevA.98.062325 [Cited within: 1]
DOI:10.1063/1.3610677 [Cited within: 1]
DOI:10.1103/PhysRevLett.85.441 [Cited within: 1]
